If you’ve tried accessing the site over the past couple of weeks, you might have noticed it wasn’t up 100% of the time. That’s because I was upgrading my network infrastructure. Before the migration, I ran the Ubiquiti EdgeRouter 6p. This is a tremendous little quad-core router that ran completely silently. I upgraded from the older ER-X when I moved from cable to fiber. The older ER-X couldn’t shuffle packets quickly enough to let me use more than 330 MB/s.
The 6p, let me use the full gigabit in both directions! Even better, it used less than 20% of the router’s resources. Over the past six and a half years, This router grew with me as my home and lab needs grew. When my kids got their own devices, the 6p let me set up quality-of-service rules that kept their devices from negatively impacting my work environment. It also provided the added benefit of keeping buffering to a minimum for the shared AppleTV device in the living room!
As I brought on more and more IoT devices, I was able to set up VLANs to keep that traffic separate from the rest of the network. I then added a VLAN to keep all my docker containers running on a dedicated segment. As security concerns grew, the 6p also allowed me to set up multiple virtual tunnels for VPN traffic. One for personal use and one for each client that required VPN access to connect to their environments. The 6p also allowed me to control which machines in my lab connected to each VPN tunnel.
As I added more IoT devices, I also found that wifi coverage was imperfect, and I started adding Access Point Mesh devices. The first-generation access points were good for indoor use but better for exterior use. With three of them, I could cover 4 acres with a strong signal. I ended up swapping those out for Access Point U6 Mesh.
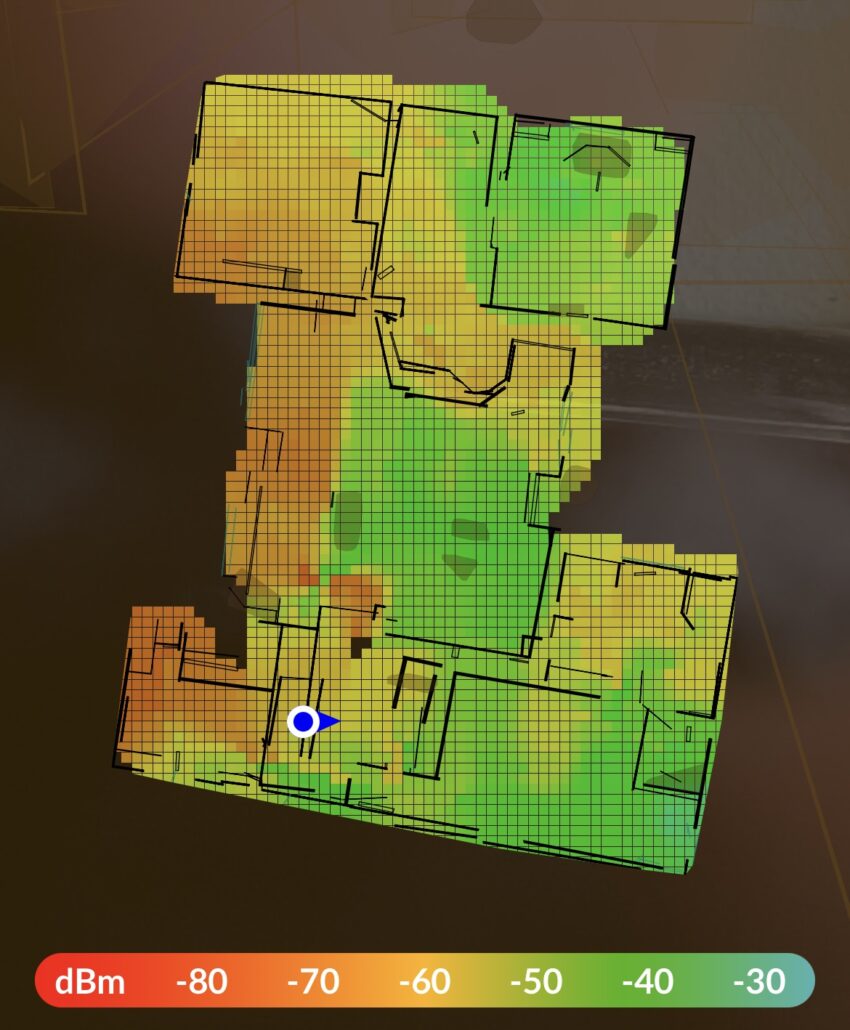
Three of them struggle to cover my home and 1-acre yard. And that problem is what prompted me to upgrade to the Dream Machine (UDM). The UDM allows me to map out wifi coverage with Augmented Reality!
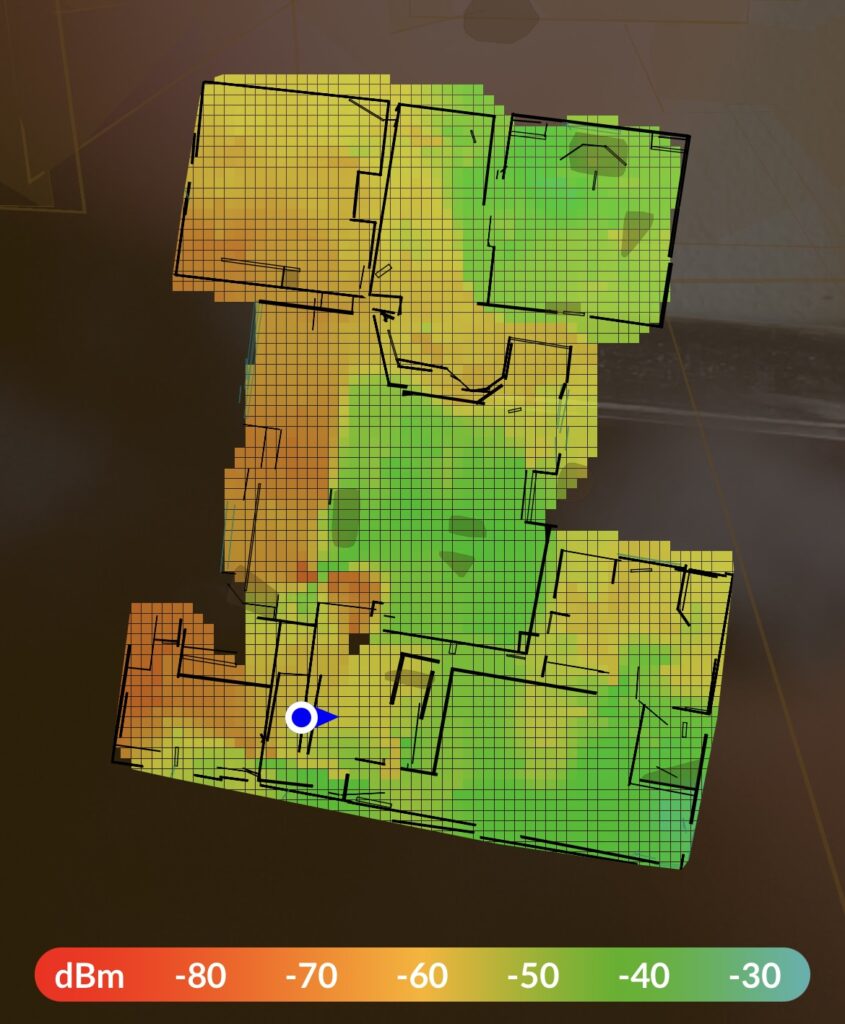
With this new feature, I can place my access points in better positions to improve my coverage. So, I ordered my new Dream Machine SE and set out to migrate my network.
The beginning of my bumpy road
When you first unpack the UDM and power it on, you’ll notice it requires an internet connection to start the setup process. Not just a network connection but a full-access connection to the internet. It turns out that UI devices reach out to a domain name blocked by my pihole. Once I disabled ad blocking, I could get an IP address and continue setup. For what it’s worth, I also have to disable ad blocking to get ring devices to bind to my ring app.
Setting up VLANs in the new Unifi OS 7.3.76 is prettier than it was setting it up in the old Edgemax. With just a few clicks I had my four VLANs ready to go.
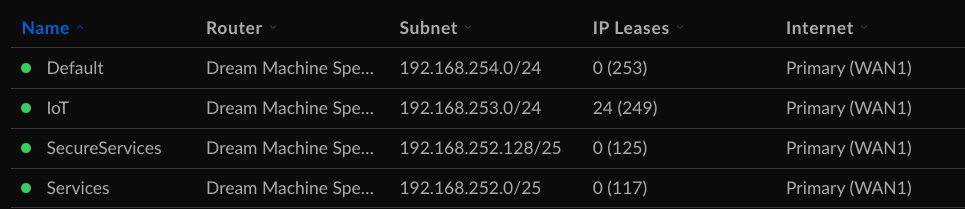
By default, each VLAN will have a DHCP server stood up to hand out IP addresses in the correct range. In my case, I turned off the auto-scale network, so I could set the IP address and range I wanted each VLAN to use. For my default and IoT networks, I left DHCP on. For my Services and SecureServices VLANs, I turned that off. All services get a static IP.
I could also set up two separate SSIDs in just a few clicks.
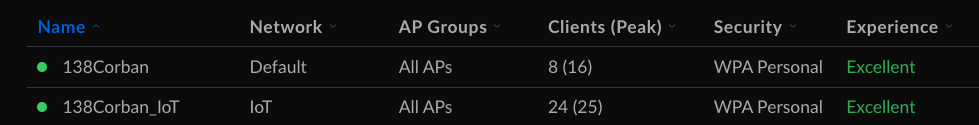
The great thing about this tool is I can attach an SSID to one of my VLANS, and devices using that SSIS automatically get an IP address in the associated IP range! So when I set the network on my 138Corban_IoT SSIS to IoT, all my devices will automatically get a 192.168.253/0/24 address. Similarly, when devices hit 138Corban, they get an address from my default range, 192.168.254.0/24.
For wired devices, you must go to the port settings on a Ubiquiti device and attach that port to your VLAN. In this case, My dual nic server uses one of those NICs to support Services and the other to support SecureServices. Here’s eth0 connected to a port that will connect to the Services VLAN.
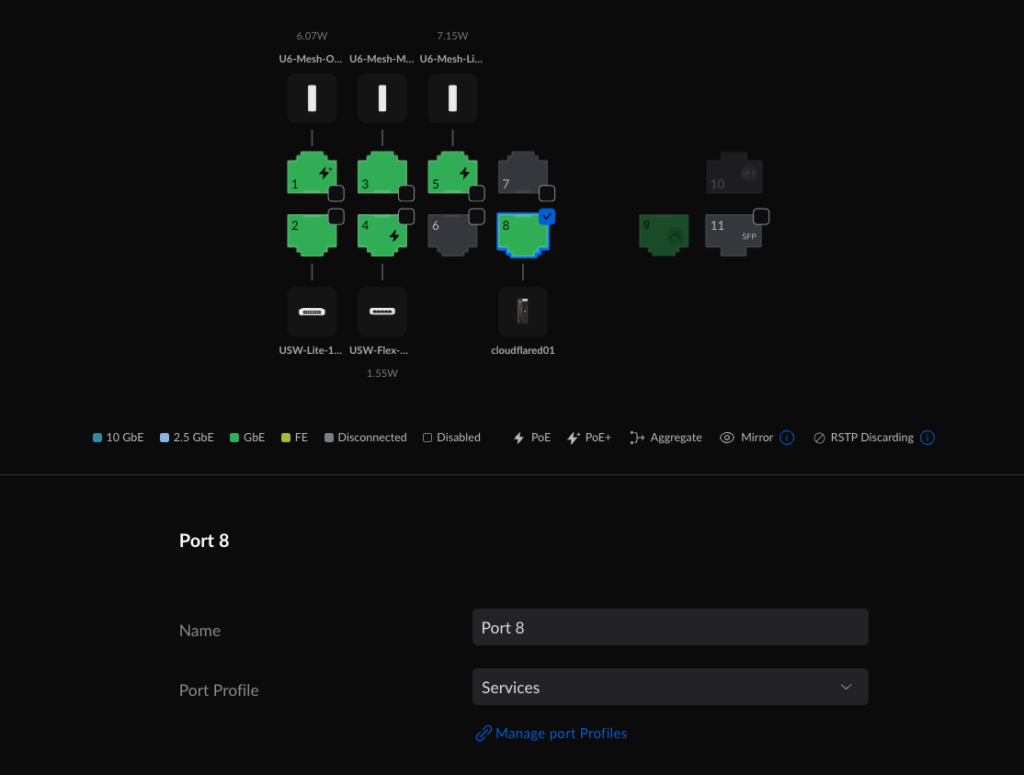
And eth1 connecting to a port attached to the SecureServices VLAN.
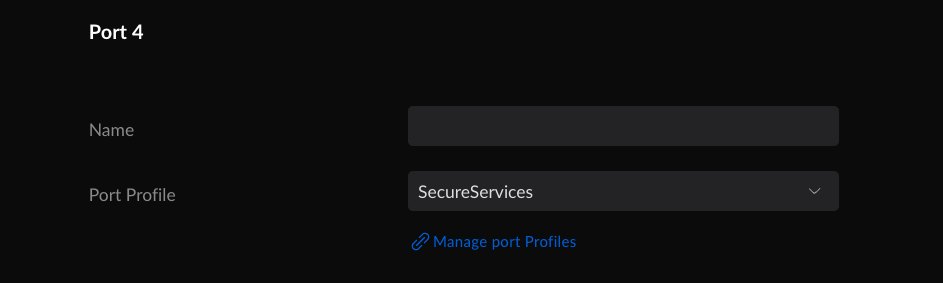
That’s when I hit the most challenging bug. From Default, I could ping any other device in the default or IoT VLANs, but I couldn’t reach any Services or SecureServices. I spent most of my free time that first week digging through the Firewall & Security settings in the new interface.
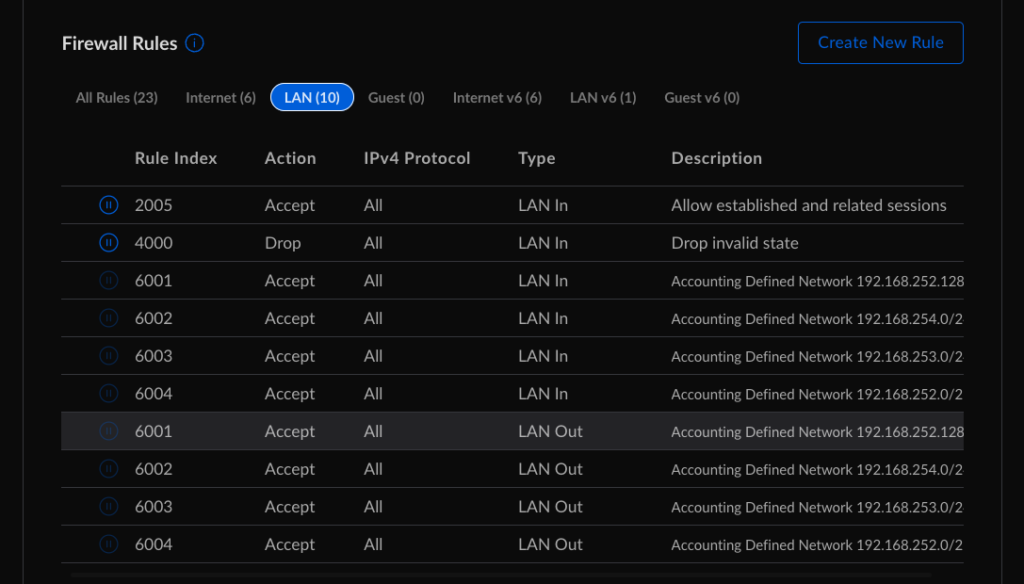
The Ubiquiti forums and helpdesk people tried their best to walk me through different options. I’d turn off the Allow established and related sessions and drop invalid state rules. That didn’t work. I also tried turning on a Traffic Management rule to allow All traffic coming out of Default to access any other network device. That didn’t work, either. The odd thing that made it start working is I had to turn DHCP on for Services and SecureServices for a few hours. Once I could reach Services and SecureServices from Default, I turned DHCP back off. Traffic continues to flow over a week later.
Up and running… mostly
Once I could communicate with my Services VLAN, I noticed other issues managing my upgraded network. Unifi OS doesn’t use pihole to reverse lookup on IP address/mac address to the device name. And it also doesn’t like to act as a secondary DNS server either. I also discovered my docker environment was a little too tightly coupled with my old network settings. In the next few blog entries, I’ll share the other bumps I had to solve to get everything back up and running in my lab environment. In the meantime, if you have any questions, let me know.